Data requirements for "What is our application portfolio?"
This business question examines the application portfolio. The visualization is a master list of all applications and their attributes and relationships to other aspects of the IT architecture.
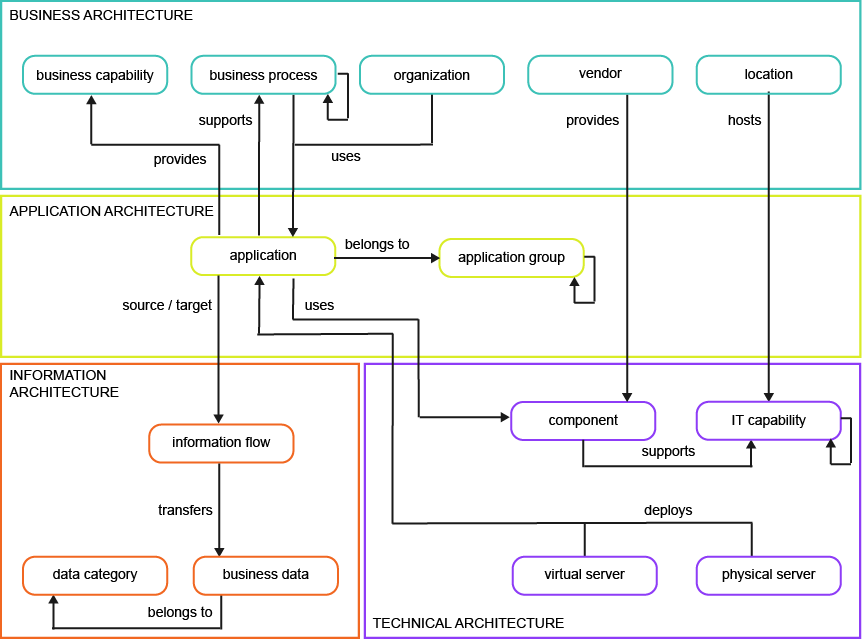
To have meaningful data for the business question What is our application portfolio?, you must capture the following information about the applications in your company.
| Column | Mandatory | Explanation |
|---|---|---|
|
Name |
x |
The application name. |
|
Short Name |
A short name to identify the application. |
|
|
Version |
x |
The application version. |
|
Description |
A short description of the application. |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retired when the application's end data is reached. |
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
| Architecture Type |
The architecture type of the application: Possible values are:
|
|
|
Development Type |
The application development type.
|
|
|
Authentication |
The authentication method used for the application.
|
|
|
Alias |
A unique suffix used to identify this application. |
|
|
Recommendation |
The strategic recommendation regarding future investment for the application. Possible values are:
|
|
|
Strategic |
Indicates whether the application is strategic for the business. |
|
| Pace-Layered Governance |
Classification of application according to the Pace-Layered Application Strategy. Possible values are:
|
|
|
Predecessor |
The application's predecessor application. |
|
|
Successor |
The application's successor application. |
|
|
Cloud Migration Strategy |
The strategy to migrate the application to the cloud. Possible values include:
|
|
|
Subject to Compliance Regulation |
Indicates whether the application is bound to compliance regulations. This is relevant for cloud migration analytics. |
|
|
Authorized User Group |
The user groups who have access permissions to the application. |
|
|
Organization: Business Owner |
An organization who owns the application and is responsible for managing the functional requirements. |
|
|
Organization: IT Owner |
An IT organization owning the application and thus typically responsible for approval decisions. |
|
|
Organization: Operations |
An IT organization responsible for the operations of the application. |
|
|
Organization: Stakeholder |
An organization that has an interest in the application and therefore requires read-only access permissions. |
|
|
Person / User: Application Manager |
A person who is the subject matter expert for the application from a functional and technical point of view. |
|
|
Person / User: Architect |
A person who is responsible for the governance of the application. |
|
|
Person / User: Business Owner |
A person who owns the application and is responsible for managing the functional requirements. |
|
|
Person / User: IT Owner |
A person owning the application and thus typically responsible for approval decisions. |
|
|
Person / User: Stakeholder |
A person that has an interest in the application and therefore requires read-only access permissions. |
|
|
Application Assessment: Geographical Reach |
An application's area of usage and distribution reach. This allows you to determine the geographical reach of your portfolio based on application local, regional, or global usage. .
|
|
|
Application Assessment: Mobile Capability |
Mobile capability is used to determine whether an application is complaint for mobile platforms. An application that fully supports all mobile platforms (Smartphones, Tablets, Smart TVs, Smart Watches, etc.) is considered to be fully mobile-compliant. An application supporting one or many but not all of the mobile platforms is considered to partially mobile-compliant.
|
|
|
Application Assessment: Multi Language Support |
Indicates the level of support an application provides for multiple languages: 0- Unknown, 1- No, 2- Yes |
|
|
Application Assessment: Number of Users |
Indicates the number of users using this application.
|
|
|
Application Assessment: SCA Compliance |
Strong Customer Authentication (SCA) is a European regulatory requirement to reduce fraud and make online payments more secure. SCA requires authentication to use at least two of the following three elements: 1. Something the customer knows (PIN/Password), 2. Something the customer has (Phone/Hardware token), 3. Something the customer is (Fingerprint/Face recognition). Possible values are: 0- Not required, 1- No but required, 2- Yes | |
|
Application Classification: 1 Confidentiality |
1-Not Critical 2-Essential 3-Critical. |
|
|
Application Classification: 2 Integrity |
1-Not Critical 2-Essential 3-Critical. |
|
|
Application Classification: 3 Availability |
1-Not Critical 2-Essential 3-Critical. |
|
|
Application Classification: DPIA Rating |
A data protection impact assessment (DPIA) is a privacy-related assessment whose objective is to identify and analyze certain actions or activities that might affect data privacy. Under the GDPR regulations, data protection impact assessments are mandatory in certain cases such as when profiling activities are carried out using personal data. Possible values are: 5- Very High, 4- High, 3- Medium, 2- Low, 1- Very Low, 0- Not Required |
|
|
Disaster Recovery: Recovery Point Objective (Hrs) |
Indicates the recovery point objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
|
|
Disaster Recovery: Recovery Time Objective (Hrs) |
Indicates the recovery time objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
|
|
Cloud Assessment: Does the app have peaks in the workload? |
1-No 2-Yes (Exceptionally) 3-Yes (Regularly). |
|
|
Cloud Assessment: Is the license eligible for cloud? |
1-No 2-Yes. |
|
|
Plan Start Date |
This is the start date of the lifecycle phase Plan. The end date will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Pilot Start Date |
This is the start date of the lifecycle phase Pilot. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Production Start Date |
This is the start date of the lifecycle phase Production. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Sunset Start Date |
This is the start date of the lifecycle phase Sunset. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Retired Start Date |
Start Date of "Retired" Phase. The End Date of the "Retired" Phase will be set to the Lifecycle End Date. This is the start date of the lifecycle phase Retired. The end date will be set to the lifecycle end date. |
|
|
Lifecycle End Date |
This is the end date of the last lifecycle phase. |
|
|
Business Process |
The business processes that the application supports. |
|
|
supported Business Capability |
x |
The business capabilities that the application provides. |
|
using Business Capability |
The business capabilities that use the application. |
|
|
using Organization |
x |
The organizations that use the application. |
|
Application Group |
The application groups that the application is assigned to. |
|
|
Component |
x |
The components that help provide the application. |
|
Vendor |
The vendors that indirectly provide the application via the components that the vendor provides. |
|
|
Physical Server, Virtual Server |
x |
The virtual and physical servers that the application runs on. |
|
Location |
The location of the application based on the location of the physical/virtual server that it runs on. |
|
|
upstream Application |
x |
Indirect reference via an incoming information flow. |
|
downstream Application |
x |
Indirect reference via an outgoing information flow |
|
Business Data |
x |
Indirect reference via business data usage. |