Data requirements for "What are our architectural dependencies?"
This business question examines the dependencies that applications have to other applications based on their information flows.
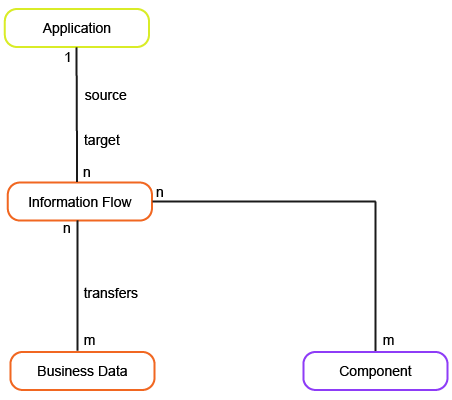
To have meaningful data for the business question What are our architectural dependencies?, you must capture the following information about the applications and information flows in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
Necessary for the visualization. |
||
|
Version |
Necessary for the visualization. |
||
|
Object State |
Required for business question |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are: |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer actively used. |
|
|
Status |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
||
|
Architecture Type |
Required for business question |
The architecture type of the application: Possible values are:
|
|
|
Development Type |
Required for business question |
The application development type.
|
|
|
Authentication |
Required for business question |
The authentication method used for the application.
|
|
|
Recommendation |
Required for business question |
The strategic recommendation regarding future investment for the application. Possible values are:
|
|
|
Information Flow |
|||
|
Name |
The name is a concatenation of <Source Application> >> <Target Application>. |
||
|
Connection Method |
Required for business question |
A connection method describes the mode of transfer used by a specific information flow to transfer business data between the two associated applications or their respective components. Preconfigured connection methods include: Middleware, P2P, Other |
|
|
Connection Frequency |
Required for business question |
A connection frequency describes how often a specific information flow is used to transfer business data between the two associated applications or their respective components. Preconfigured connection frequencies include: Hourly, Daily, Weekly, Monthly, Quarterly, Yearly, Real Time, On Demand, Other |
|
|
Connection Data Format |
Required for business question |
A connection data format describes the data format used for the transfer of business data via a specific information flow. Preconfigured connection data formats include: ASCII, Binary, CSV, IDoc, Other |
|
|
Connection Data Type |
Required for business question |
A connection type describes the mode of transfer used by a specific information flow to transfer business data between the two associated applications or their respective components. Preconfigured connection types include: Asynchronous, Synchronous, Other |
|
|
Source Application |
x |
An information flow requires an application that is the source of the connection. |
|
|
Target Application |
x |
An information flow requires an application that is the target of the data exchange. |
|