What is our technical debt?
-
Use the method that is most convenient for you:
- In the left navigation panel, enter What is our technical debt? in the Search Navigation field.
- In the left navigation panel, click Home. In the content area, go to the Business Questions page and click the tile for What is our technical debt?
- In the left navigation panel, expand the sections Business Questions and Transparency and click What is our technical debt?
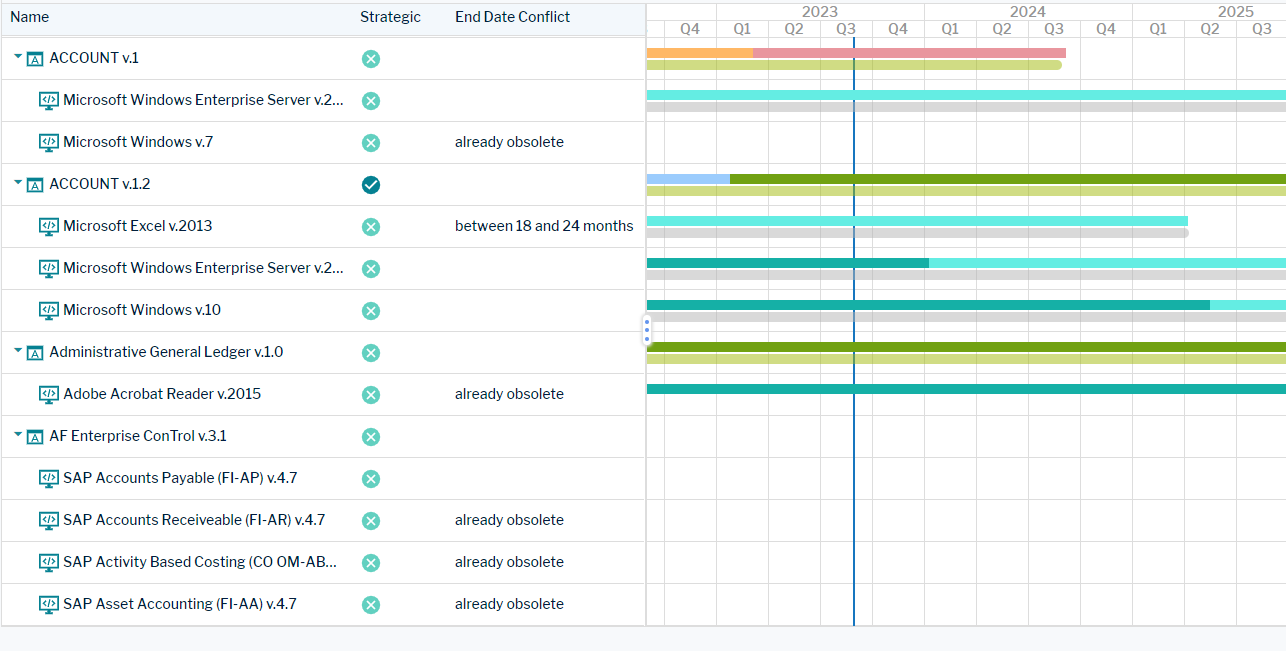
The business question What is our technical debt? focuses on the critical dependence that an application has to the technological component that it relies on to run. Lifecycle information provides insight to potential conflicts and risks due to end-of-life technologies. Identify at-risk applications that are critical to the business and derive the necessary measures to mitigate potential risk before an application or component goes out of service.
This business question visualizes applications and the components they use in a Gantt chart. A green bar represents the application's start and end dates. The application's lifecycle phases may be displayed by a multi-colored bar below the green bar. Likewise, a grey bar indicates the component's start and end dates and a multi-colored bar may be displayed if a component's lifecycle phases are defined.
Mature organizations may have a lifecycle planning practice and capture the phases of a lifecycle. Application lifecycle phases may include: Plan, Pilot, Production, Sunset, Retired.
Component lifecycle phases are typically based on the vendor support. Component lifecycle phases may include: Manufacturer Supported and Manufacturer Extended Support.
A symbol indicates whether an application is strategic for the business as well as information about potential conflicts in application support. The End Date Conflict column provides information if the end date of a component will be reached before the end date of the application that depends on the component.
With this information, you can address the technical debt before an application or component goes out of service and prioritize applications that require immediate migration. This business question ensures that you effectively plan the most urgent requirements for application migration or updates that are important for regulatory requirements.
Which application will retire soon and may require a technology migration plan? Sort the data based on the application end date to understand which applications require immediate attention. Click the Filter ![]() button and set End Date in the Sort Order field. The applications that are are most critical for the business will have a checkmark in the Strategic column.
button and set End Date in the Sort Order field. The applications that are are most critical for the business will have a checkmark in the Strategic column.
Which active applications are running on obsolete components or use components that will soon go out of service? Click the Filter ![]() button and select Active in the Object State field and already obsolete in the Lifecycle Conflict field. Identify the applications that have no component support and contact the authorized user to understand whether they can be sundowned.
button and select Active in the Object State field and already obsolete in the Lifecycle Conflict field. Identify the applications that have no component support and contact the authorized user to understand whether they can be sundowned.
Set within six months in the Lifecycle Conflict field to understand which technologies require immediate attention. Consider which applications are most at risk due to end-of-life technologies and make plans to mitigate the risk of running unsupported applications.
What is the impact of potential lifecycle conflicts for specific aspects of the business? Click the Filter ![]() button and select a business capability in the Business Capabilities field to show only the applications supporting that business capability. Recommendation: Review the End Date Conflict column and look for applications with the values already obsolete and within six months to determine which business capabilities are at risk based on end-of-life technologies.
button and select a business capability in the Business Capabilities field to show only the applications supporting that business capability. Recommendation: Review the End Date Conflict column and look for applications with the values already obsolete and within six months to determine which business capabilities are at risk based on end-of-life technologies.
What is the impact of potential lifecycle conflicts for a specific organization? Click the Filter ![]() button and select an organization in the Business Owner field to show only applications owned by the organization. Recommendation: Contact the business owner organization so that they are aware that components that their applications use may soon be obsolete.
button and select an organization in the Business Owner field to show only applications owned by the organization. Recommendation: Contact the business owner organization so that they are aware that components that their applications use may soon be obsolete.
What is the impact of potential lifecycle conflicts for a specific application portfolio? Click the Filter ![]() button and select an application group in the Application Group field to show the applications assigned to the application group. Review which applications may be at risk because the components that they use may soon be obsolete.
button and select an application group in the Application Group field to show the applications assigned to the application group. Review which applications may be at risk because the components that they use may soon be obsolete.