Capture data for business questions (Simplified)
Data can be most easily collected in the Excel Roundtrip view which allows you to capture data for specific business questions without the need to configure data capture templates. An XLSX file can be generated for each object class and reference that is relevant for a business question.
The generated XLSX file only includes columns for the attributes, referenced objects, indicators, and roles that are necessary for the business question. Once you have captured your data in the XLSX file, you can upload it and then check the completeness and quality of your data in the context of a business question. Here you can see immediately the quality of your data and correct any data quality issues.
- Go to Data Import > Excel Roundtrip.
- Click the filter symbol and select a business question in the Business Question field and click Update. Alternatively you can select a class in the Class field.
- The data should be defined in numerical order, starting with the classes that have the smallest numbers displayed in the lower right corner of the boxes.
- Select an object class element and click Generate XLSX File.
- Select a reference element visualized as a black arrow between the object class elements and click Generate XLSX File.
- Capture the data in each XLSX file as described in the section Data import workflow with XLSX files.
- Click Data Capture > Upload Data Capture File.
- Click Data Capture > Open Data Capture Status Report to check the success of your data import.
- Change to the Portfolio Manager user profile and go to the business question that you are capturing the data for to check the data quality of the business question.
Business capabilities and applications must be in the repository. The reference between business capabilities and the applications that support them must be specified.
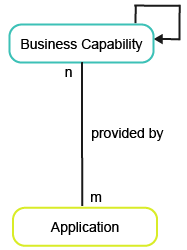
The following table lists the attributes required for each object class in order to have meaningful data for the business question What should we be focusing on?:
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Business Capability |
This business question requires the availability of at least 2 levels of business capabilities in your portfolio. |
||
|
Level ID |
The hierarchical number of the business capability in the business capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. Necessary for the visualization. |
||
|
Name |
x |
The level ID and name of the business capability is displayed in the boxes of the heat map. |
|
|
Business Relevance |
Required for business question |
Indicates how relevant the business capability is for the business:
|
|
|
Parent Business Capability |
Every business capability on the second level of the hierarchy and lower should have a parent business capability defined. This enables the aggregation of applications that provide a lower-level business capability up to the second-level business capability. |
||
|
Application |
|||
|
Name |
x |
The name of the application. |
|
|
Start Date |
The start date is the date when the application is actively used. |
||
|
End Date |
The end date is the date when the application is no longer used. |
||
| Object State |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
||
|
Status |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
||
|
Recommendation |
Required for business question |
The strategic recommendation regarding future investment for the application. Possible values are:
|
|
|
Strategic Application |
Indicates whether the application is strategic for the business. |
||
|
Reference for Application provides Business Capability |
Required for business question | ||
|
Business Capability |
The business capability that is supported by the application. | ||
|
Application |
The application supporting the business capability. |
In Alfabet FastLane, responsibilities are documented via the concept of roles whereby each role is based on either a preconfigured role type or a custom role type configured by your company. Click for details about how to configure additional role types for your company.
This business question requires users and organizations to be in the repository as well as the applications and components that you want to define roles for.
The following table lists the information required in order to have meaningful data for the business question Who is responsible for our assets?:
| Class | Explanation |
|
Assets |
The data capture template focuses on capturing responsibilities for the object classes Application and Component. However, responsibilities can be captured in Alfabet FastLane for almost all object classes. |
|
Role |
A role references the asset, the responsible person or organization, and the role type that the role is based on. |
|
Role Type |
Role types are preconfigured. The configuration includes the object classes for which the role types are available as well as whether the role can be filled by a single user and/or organization or multiple users and/or organizations. The following preconfigured role types are available:
|
|
Person |
The user that is responsible to fulfill the role for the object. |
|
Organization |
The organization that is responsible to fulfill the role for the object. |
This business question helps to assess whether components are aligned with the standards catalog to support the company's IT capabilities.
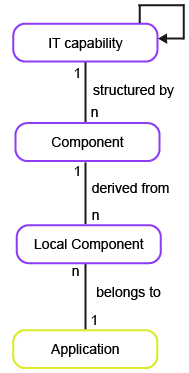
To have meaningful data for the business question What is our standards catalog?, you must capture the following information about the components and IT capabilities in your company.
| Class | Attribute | Mandatory | Explanation |
|
Component |
Name |
x |
Necessary for the visualization. |
|
Version |
x |
Necessary for the visualization. |
|
|
Start Date |
The start date is the date when the component is actively used. |
||
|
End Date |
The end date is the date when the component is no longer actively used. |
||
|
Object State |
Describes the operational status of the component and indicates whether it is actively used, planned to be used, or has been used in the past. Possible values are:
|
||
|
Strategic Component |
Specifies whether the component is strategic. |
||
|
Support Model |
The business support model for the component. Possible values are:
|
||
|
Standardization |
Required for business question |
Specify whether the component is a standard component. This helps you to promote the use of standard components and reduce non-standard technologies. Possible values are:
|
|
|
IT Capability |
x |
A component is assigned to the IT capability it supports. |
|
|
IT Capability |
Level ID |
The hierarchical number of the IT capability in the IT capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. Necessary for the visualization. |
|
|
Name |
x |
Necessary for the visualization. |
|
|
Parent IT Capability |
The parent IT capability relationship is used to aggregate components assigned to a lower-level IT capability to the second-level IT capability in the IT capability hierarchy. |
||
This business question focuses on the roles Business Owner and IT Owner in the company and examines which organizations have responsibility for applications. The best-practice recommendation is that a business owner and IT owner are documented for every application.
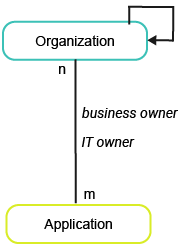
To have meaningful data for the business question Who owns which applications?, you must import and capture the following information about the applications and organizations in your company:
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
x |
The name of the application. |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
| Object State |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
||
|
Status |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
||
|
Organization: Business Owner |
Required for business question |
The role Business Owner is responsible for managing the functional requirements of application. |
|
|
Organization: IT Owner |
Required for business question |
The role IT Owner is typically responsible for approval decisions about the applications. |
|
|
Organization |
|||
|
Name |
x |
The name of an organization. |
|
|
Parent Organization |
Every organization on the second level of the hierarchy and lower should have a parent organization defined. This enables the aggregation of applications that are owned by a lower-level organization up to the second-level organization. |
||
This business question examines all projects including their lifecycle information, current year budget, architecture impact, business value, and project risk.
To have meaningful data for the business question What are our most important projects?, you must capture the following information about the projects in your company.
| Class | Attribute | Mandatory | Explanation | |
|---|---|---|---|---|
|
Project |
||||
|
Name |
||||
|
Start Date |
The date that the project starts. |
|||
|
End Date |
x |
The date that the project ends. |
||
|
Status |
x |
The approval status of the project. |
||
|
Project Risk |
x |
An evaluation type based on the indicator types Duration, Team Size, and Technology Adoption. |
||
|
Business Value |
x |
An evaluation type based on Cost Saving, Market Opportunity, and Strategic Value. |
||
|
Architectural Impact |
x |
An evaluation type based on Complexity Reduction, IOnnovation, and Standards Standards Conformity. |
||
|
Monitoring Budget |
x |
Project evaluation indicator to monitor whether the project is within budget. Contributes to the calculation of the RAG Status. |
||
|
Monitoring Resource |
x |
Project evaluation indicator to monitor whether the project is within the resource allocation. Contributes to the calculation of the RAG Status. |
||
|
Monitoring Time |
x |
Project evaluation indicator to monitor whether the project is on time. Contributes to the calculation of the RAG Status. |
||
| Project Group | ||||
|
Name |
The project portfolio that that bundles the project. | |||
This business question provides and overview of the project time schedule including milestones and project dependencies.
To have meaningful data for the business question What is our project portfolio roadmap?, you must capture the following information about the projects in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Project |
|||
|
Name |
|||
|
Start Date |
The date that the project starts. |
||
|
End Date |
x |
The date that the project ends. |
|
|
Status |
x |
The approval status of the project. |
|
|
Project Group |
|||
|
Name |
|||
This business question examines the application portfolio. The visualization is a master list of all applications and their attributes and relationships to other aspects of the IT architecture.
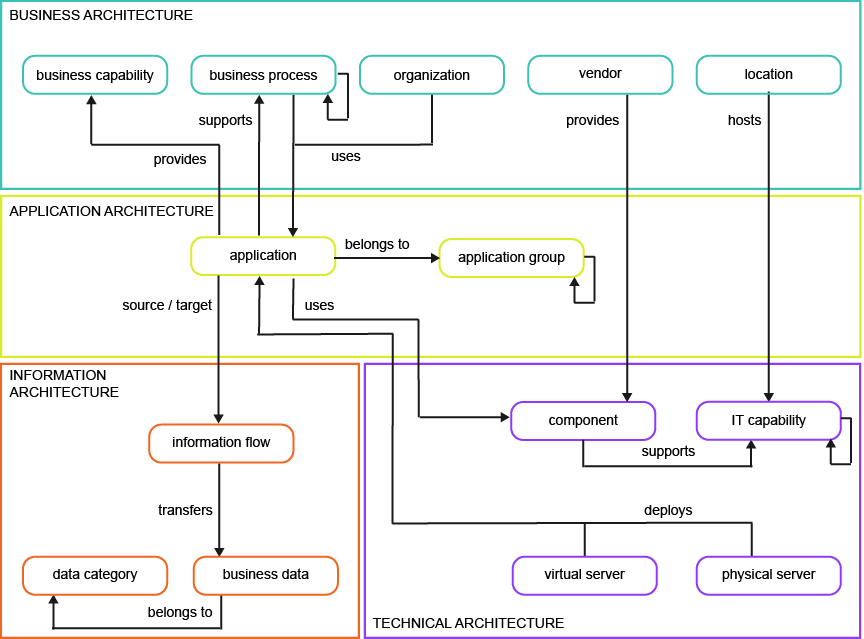
To have meaningful data for the business question What is our application portfolio?, you must capture the following information about the applications in your company.
| Column | Mandatory | Explanation |
|---|---|---|
|
Name |
x |
The application name. |
|
Short Name |
A short name to identify the application. |
|
|
Version |
x |
The application version. |
|
Description |
A short description of the application. |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
| Architecture Type |
The architecture type of the application: Possible values are:
|
|
|
Development Type |
The application development type.
|
|
|
Authentication |
The authentication method used for the application.
|
|
|
Alias |
A unique suffix used to identify this application. |
|
|
Recommendation |
The strategic recommendation regarding future investment for the application. Possible values are:
|
|
|
Strategic |
Indicates whether the application is strategic for the business. |
|
| Pace-Layered Governance |
Classification of application according to the Pace-Layered Application Strategy. Possible values are:
|
|
|
Predecessor |
The application's predecessor application. |
|
|
Successor |
The application's successor application. |
|
|
Cloud Migration Strategy |
The strategy to migrate the application to the cloud. Possible values include:
|
|
|
Subject to Compliance Regulation |
Indicates whether the application is bound to compliance regulations. This is relevant for cloud migration analytics. |
|
|
Authorized User Group |
The user groups who have access permissions to the application. |
|
|
Organization: Business Owner |
An organization who owns the application and is responsible for managing the functional requirements. |
|
|
Organization: IT Owner |
An IT organization owning the application and thus typically responsible for approval decisions. |
|
|
Organization: Operations |
An IT organization responsible for the operations of the application. |
|
|
Organization: Stakeholder |
An organization that has an interest in the application and therefore requires read-only access permissions. |
|
|
Person / User: Application Manager |
A person who is the subject matter expert for the application from a functional and technical point of view. |
|
|
Person / User: Architect |
A person who is responsible for the governance of the application. |
|
|
Person / User: Business Owner |
A person who owns the application and is responsible for managing the functional requirements. |
|
|
Person / User: IT Owner |
A person owning the application and thus typically responsible for approval decisions. |
|
|
Person / User: Stakeholder |
A person that has an interest in the application and therefore requires read-only access permissions. |
|
|
Application Assessment: Geographical Reach |
An application's area of usage and distribution reach. This allows you to determine the geographical reach of your portfolio based on application local, regional, or global usage. .
|
|
|
Application Assessment: Mobile Capability |
Mobile capability is used to determine whether an application is complaint for mobile platforms. An application that fully supports all mobile platforms (Smartphones, Tablets, Smart TVs, Smart Watches, etc.) is considered to be fully mobile-compliant. An application supporting one or many but not all of the mobile platforms is considered to partially mobile-compliant.
|
|
|
Application Assessment: Multi Language Support |
Indicates the level of support an application provides for multiple languages: 0- Unknown, 1- No, 2- Yes |
|
|
Application Assessment: Number of Users |
Indicates the number of users using this application.
|
|
|
Application Assessment: SCA Compliance |
Strong Customer Authentication (SCA) is a European regulatory requirement to reduce fraud and make online payments more secure. SCA requires authentication to use at least two of the following three elements: 1. Something the customer knows (PIN/Password), 2. Something the customer has (Phone/Hardware token), 3. Something the customer is (Fingerprint/Face recognition). Possible values are: 0- Not required, 1- No but required, 2- Yes | |
|
Application Classification: 1 Confidentiality |
1-Not Critical 2-Essential 3-Critical. |
|
|
Application Classification: 2 Integrity |
1-Not Critical 2-Essential 3-Critical. |
|
|
Application Classification: 3 Availability |
1-Not Critical 2-Essential 3-Critical. |
|
|
Application Classification: DPIA Rating |
A data protection impact assessment (DPIA) is a privacy-related assessment whose objective is to identify and analyze certain actions or activities that might affect data privacy. Under the GDPR regulations, data protection impact assessments are mandatory in certain cases such as when profiling activities are carried out using personal data. Possible values are: 5- Very High, 4- High, 3- Medium, 2- Low, 1- Very Low, 0- Not Required |
|
|
Disaster Recovery: Recovery Point Objective (Hrs) |
Indicates the recovery point objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
|
|
Disaster Recovery: Recovery Time Objective (Hrs) |
Indicates the recovery time objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
|
|
Cloud Assessment: Does the app have peaks in the workload? |
1-No 2-Yes (Exceptionally) 3-Yes (Regularly). |
|
|
Cloud Assessment: Is the license eligible for cloud? |
1-No 2-Yes. |
|
|
Plan Start Date |
This is the start date of the lifecycle phase Plan. The end date will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Pilot Start Date |
This is the start date of the lifecycle phase Pilot. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Production Start Date |
This is the start date of the lifecycle phase Production. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Sunset Start Date |
This is the start date of the lifecycle phase Sunset. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
|
|
Retired Start Date |
Start Date of "Retired" Phase. The End Date of the "Retired" Phase will be set to the Lifecycle End Date. This is the start date of the lifecycle phase Retired. The end date will be set to the lifecycle end date. |
|
|
Lifecycle End Date |
This is the end date of the last lifecycle phase. |
|
|
Business Process |
The business processes that the application supports. |
|
|
supported Business Capability |
x |
The business capabilities that the application provides. |
|
using Business Capability |
The business capabilities that use the application. |
|
|
using Organization |
x |
The organizations that use the application. |
|
Application Group |
The application groups that the application is assigned to. |
|
|
Component |
x |
The components that help provide the application. |
|
Vendor |
The vendors that indirectly provide the application via the components that the vendor provides. |
|
|
Physical Server, Virtual Server |
x |
The virtual and physical servers that the application runs on. |
|
Location |
The location of the application based on the location of the physical/virtual server that it runs on. |
|
|
upstream Application |
x |
Indirect reference via an incoming information flow. |
|
downstream Application |
x |
Indirect reference via an outgoing information flow |
|
Business Data |
x |
Indirect reference via business data usage. |
This business question allows you to understand the dependence of the applications on components based on component and application lifecycles so that you can act on your technical debt before the application or component goes out of service.
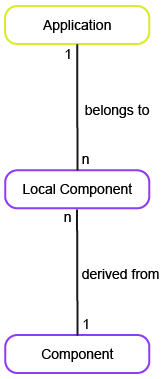
To have meaningful data for the business question What is our technical debt?, you must capture the following information about the applications and components in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
|||
|
Version |
|||
|
Start Date |
The start date is the date when the application is actively used. |
||
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Strategic Application |
Indicates whether the application is strategic for the business. |
||
|
Lifecycle |
Application lifecycle phases may include: Plan, Pilot, Production, Sunset, Retired | ||
|
Local Component |
|||
|
Application |
x |
The local component is used by the application it belongs to. |
|
|
Component |
The local component is derived from a component. |
||
|
Component |
|||
|
Name |
|||
|
Version |
|||
|
Object State |
Indicates whether the component is planned, currently active, or retired. Retired components are not displayed in the report. |
||
|
Start Date |
x |
The start date is the date when the component is actively used. |
|
|
End Date |
x |
The end date is the date when the component is no longer supported. |
|
|
Strategic Component |
Indicates whether the component is strategic for the business. |
||
|
Lifecycle |
Component lifecycle phases include Manufacturer Supported and Manufacturer Extended Support. | ||
The business question Who are our vendors? provides an overview of the vendors that support your IT portfolio.
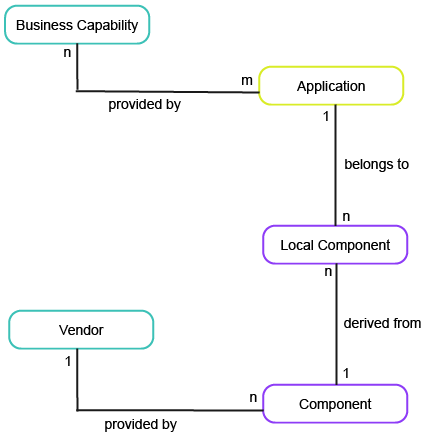
To have meaningful data for the business question, you must capture data for vendors as well as the components they provide, the applications that use the components, and the business capabilities that the applications support.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
Necessary for the visualization. |
||
|
Version |
Necessary for the visualization. |
||
|
Object State |
Describes the operational status of the application. Applications with a retired object state are ignored. |
||
|
Business Capability |
|||
|
Level ID |
Indicates the hierarchical number of the business capability in the business capability hierarchy. |
||
|
Name |
|||
|
Business Relevance |
x |
Indicates how relevant the business capability is for the business. |
|
|
Application |
x |
Application providing the business capability |
|
|
Local Component |
|||
|
Application |
The local component is used by the application it belongs to. |
||
|
Component |
The component that the local component is derived from. |
||
|
Component |
|||
|
Name |
|||
|
Version |
|||
|
Object State |
Describes the operational status of the component. |
||
|
Lifecycle |
x |
The component lifecycle begins with the start date and concludes with the end date. |
|
|
Vendor |
x |
The vendor providing the component. |
|
|
Vendor |
|||
|
Name |
This is necessary for the visualization. |
||
This business question examines the dependencies that applications have to other applications based on their information flows.
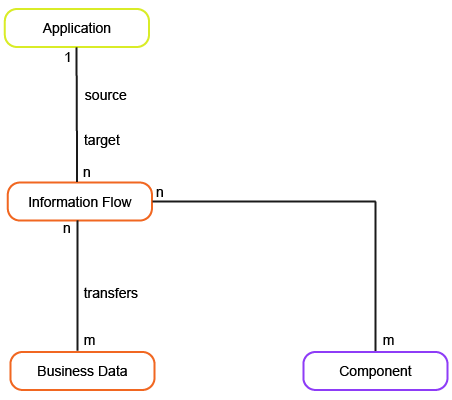
To have meaningful data for the business question What are our architectural dependencies?, you must capture the following information about the applications and information flows in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
Necessary for the visualization. |
||
|
Version |
Necessary for the visualization. |
||
|
Object State |
Required for business question |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are: |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer actively used. |
|
|
Status |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
||
|
Architecture Type |
Required for business question |
The architecture type of the application: Possible values are:
|
|
|
Development Type |
Required for business question |
The application development type.
|
|
|
Authentication |
Required for business question |
The authentication method used for the application.
|
|
|
Recommendation |
Required for business question |
The strategic recommendation regarding future investment for the application. Possible values are:
|
|
|
Information Flow |
|||
|
Name |
The name is a concatenation of <Source Application> < <Target Application>. |
||
|
Connection Method |
Required for business question |
A connection method describes the mode of transfer used by a specific information flow to transfer business data between the two associated applications or their respective components. Preconfigured connection methods include: Middleware, P2P, Other |
|
|
Connection Frequency |
Required for business question |
A connection frequency describes how often a specific information flow is used to transfer business data between the two associated applications or their respective components. Preconfigured connection frequencies include: Hourly, Daily, Weekly, Monthly, Quarterly, Yearly, Real Time, On Demand, Other |
|
|
Connection Data Format |
Required for business question |
A connection data format describes the data format used for the transfer of business data via a specific information flow. Preconfigured connection data formats include: ASCII, Binary, CSV, IDoc, Other |
|
|
Connectioo Data Type |
Required for business question |
A connection type describes the mode of transfer used by a specific information flow to transfer business data between the two associated applications or their respective components. Preconfigured connection types include: Asynchronous, Synchronous, Other |
|
|
Source Application |
x |
An information flow requires an application that is the source of the connection. |
|
|
Target Application |
x |
An information flow requires an application that is the target of the data exchange. |
|
This business question focuses on applications and the business processes they support.
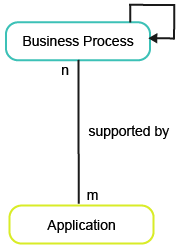
To have meaningful data for the business question Which business process areas require the most IT support?, you must import and capture the following information about the applications and business processes in your company:
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
x |
The application name. |
|
|
Version |
x |
The version number for the application. It is recommended that you document major and minor release versions (<MajorVersion.MinorVersion>). |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
|
|
Architecture Type |
The architecture type of the application: Possible values are:
|
||
|
Authentication |
The authentication method used for the application.
|
||
|
Development Type |
The application development type.
|
||
|
Recommendation |
The strategic recommendation regarding future investment for the application. Possible values are:
|
||
|
Strategic Application |
Indicates whether the application is strategic for the business. |
||
|
Application Assessment: Geographical Reach |
Indicator to evaluate an application's area of usage and distribution reach. This allows you to determine the geographical reach of your portfolio based on application local, regional, or global usage. .
|
||
|
Application Assessment: Mobile Capability |
Indicator to evaluate whether an application is complaint for mobile platforms. An application that fully supports all mobile platforms (Smartphones, Tablets, Smart TVs, Smart Watches, etc.) is considered to be fully mobile-compliant. An application supporting one or many but not all of the mobile platforms is considered to partially mobile-compliant.
|
||
|
Application Assessment: Multi Language Support |
Indicator to evaluate the level of support an application provides for multiple languages: 0- Unknown, 1- No, 2- Yes |
||
|
Application Assessment: Number of Users |
Indicator to evaluate sthe number of users using this application.
|
||
|
Application Assessment: SCA Compliance |
Strong Customer Authentication (SCA) is a European regulatory requirement to reduce fraud and make online payments more secure. SCA requires authentication to use at least two of the following three elements: 1. Something the customer knows (PIN/Password), 2. Something the customer has (Phone/Hardware token), 3. Something the customer is (Fingerprint/Face recognition). Possible values are: 0- Not required, 1- No but required, 2- Yes | ||
|
Application Classification: 1 Confidentiality |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: 2 Integrity |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: 3 Availability |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: DPIA Rating |
A data protection impact assessment (DPIA) is a privacy-related assessment whose objective is to identify and analyze certain actions or activities that might affect data privacy. Under the GDPR regulations, data protection impact assessments are mandatory in certain cases such as when profiling activities are carried out using personal data. Possible values are: 5- Very High, 4- High, 3- Medium, 2- Low, 1- Very Low, 0- Not Required |
||
|
Disaster Recovery: Recovery Point Objective (Hrs) |
Indicator to evaluate the recovery point objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
||
|
Disaster Recovery: Recovery Time Objective (Hrs) |
Indicator to evaluate the recovery time objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
||
|
Cloud Assessment: Peak Workloads |
1-No 2-Yes (Exceptionally) 3-Yes (Regularly). |
||
|
Cloud Assessment: License Eligible for Cloud |
1-No 2-Yes. |
||
|
Business Process |
|||
|
Level ID |
|||
|
Name |
The business process name. |
||
|
Parent Business Process |
The parent relationship is used to roll-up all applications supporting a lower-level business process up to the second level business process shown in the report. |
||
|
Application |
x |
One or more applications that support the business process. |
|
This business question provides an overview of your projects and their costs.
To have meaningful data for the business question What is our CAPEX distribution?, you must capture the following information about the projects in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Project |
|||
|
Name |
|||
|
Software License Cost |
The costs for software license for the project. |
||
|
Software Maintenance Cost |
x |
The costs to maintain software license for the project. |
|
|
Infrastructure Cost |
x |
The costs to deploy IT assets for the project. |
|
|
Service Cost |
x |
Other service costs in addition to the maintenance costs. |
|
|
OpEx Cost |
x |
The operating expenditures for the project. |
|
|
Year |
The project cost per year. |
||
|
Project Group |
|||
|
Name |
|||
This business question focuses on applications on multiple dimensions in the context of a TIME ( Tolerate, Invest, Migrate, Eliminate) quadrant.
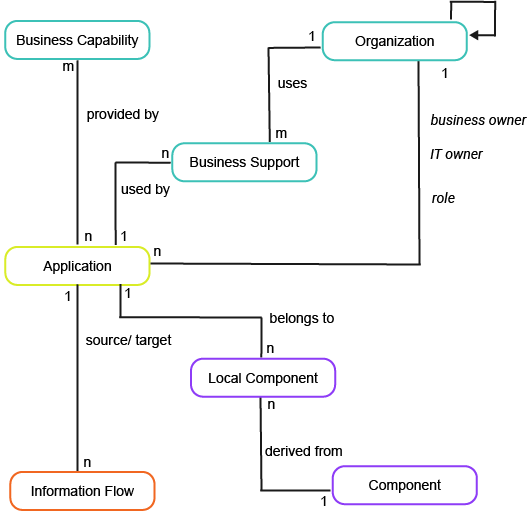
To have meaningful data for the business question What are our investment and retirement candidates?, you must capture the following information about the applications, business capabilities, organizations, application groups, information flows, and components in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
Necessary for the visualization. |
||
|
Version |
Necessary for the visualization. |
||
|
Start Date |
x |
The start state contributes to the technical score of the application. |
|
|
Recommendation |
x |
The strategic recommendation regarding future investment for the application. Possible values are:
|
|
|
Architecture Type |
x |
The architecture type of the application: Possible values are:
|
|
|
Development Type |
x |
The application development type.
|
|
|
Number of Users |
x |
Indicator specifying the number users of the application. Contributes to the application's business score.
|
|
|
Software License Cost Software Maintenance Cost Infrastructure Cost Service Cost OpEx Other |
x (all) |
The application's current year total operational expenditure (OpEx) is defined as the sum of the application costs for the current year. |
|
|
Business Owner and IT Owner |
x |
The roles business owner and IT owner must be specified for either a person or organization for an application. |
|
|
(Using) Organization |
x |
The number of organizations using the application. Contributes to the business score. |
|
|
Business Capability |
|||
|
Level ID |
The hierarchical number of the business capability in the business capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. |
||
|
Name |
Necessary for the visualization |
||
|
Business Relevance |
x |
Indicates how relevant the business capability is for the business. Contributes to the business score.
|
|
|
Application |
x |
Application providing the business capability |
|
|
Information Flow |
|||
|
Object State |
Describes the operational status of the information flow. Information flows with a retired object state are ignored. |
||
|
Source Application > Target Application |
x |
An information flow requires an application that is the source and target of the connection. The number of information flows for which the application is the source or target contributes to the technical score. |
|
|
Local Component |
|||
|
Application |
x |
The local component associates the component it is derived from with the application it belongs to. |
|
|
Component |
The component that the local component is derived from. |
||
|
Component |
|||
|
Object State |
Describes the operational status of the component. Components with a retired object state are ignored. |
||
|
Lifecycle |
x |
The earliest end date of the lifecycle phase Manufacturer Extended Support of all components assigned to applications via local component is used to calculate the Vendor Support Lifespan indicator. The Vendor Support Lifespan indicator contributes to the technical score. |
|
This business question focuses on the costs of the business capabilities based on the operational expenses of the applications that support them.
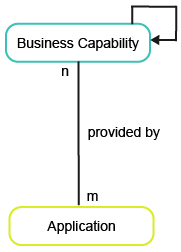
To have meaningful data for the business question What are our cost drivers?, you must capture the following information about the applications and business capabilities in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
The application's current year total operational expenditure (OpEx) per business capability is defined as the sum of the application costs for the current year divided by the number of provided business capabilities (equal cost distribution). This contributes to the size of the level 2 business capabilities. |
||
|
Software License Cost |
x |
The costs for software license for the application. |
|
|
Software Maintenance Cost |
x |
The costs to maintain software license for the application. |
|
|
Infrastructure Cost |
x |
The costs to deploy IT assets for the application. |
|
|
Service Cost |
x |
Other service costs in addition to the maintenance costs. |
|
|
OpEx Cost |
x |
The operating expenditures for the application. |
|
|
Business Capability |
This business question requires the availability of at least 2 levels of business capabilities in your portfolio. |
||
|
Level ID |
The hierarchical number of the business capability in the business capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. Necessary for the visualization. |
||
|
Name |
Necessary for the visualization. |
||
|
Business Relevance |
Required for business question. |
Indicates how relevant the business capability is for the business:
|
|
|
Parent Business Capability |
x |
Every business capability on the second level of the hierarchy and lower should have a parent business capability defined. This enables the aggregation of applications that provide a lower-level business capability up to the second-level business capability. |
|
|
Application |
x |
One or more applications that provide the business capability. |
|
This business question provides insights to the business capabilities, their dependencies, and the applications providing functional support to the business capabilities.
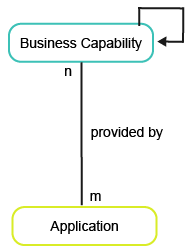
To have meaningful data for the business question What is our application landscape?, you must capture the following information about the applications and business capabilities in your company. This business question requires the availability of at-least 2 levels of business capabilities in your portfolio.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
x |
The application name. |
|
|
Version |
x |
The version number for the application. It is recommended that you document major and minor release versions (<MajorVersion.MinorVersion>). |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
|
|
Architecture Type |
The architecture type of the application: Possible values are:
|
||
|
Authentication |
The authentication method used for the application.
|
||
|
Development Type |
The application development type.
|
||
|
Recommendation |
The strategic recommendation regarding future investment for the application. Possible values are:
|
||
|
Strategic Application |
Indicates whether the application is strategic for the business. |
||
|
Application Assessment: Geographical Reach |
Indicator to evaluate an application's area of usage and distribution reach. This allows you to determine the geographical reach of your portfolio based on application local, regional, or global usage. .
|
||
|
Application Assessment: Mobile Capability |
Indicator to evaluate whether an application is complaint for mobile platforms. An application that fully supports all mobile platforms (Smartphones, Tablets, Smart TVs, Smart Watches, etc.) is considered to be fully mobile-compliant. An application supporting one or many but not all of the mobile platforms is considered to partially mobile-compliant.
|
||
|
Application Assessment: Multi Language Support |
Indicator to evaluate the level of support an application provides for multiple languages: 0- Unknown, 1- No, 2- Yes |
||
|
Application Assessment: Number of Users |
Indicator to evaluate sthe number of users using this application.
|
||
|
Application Assessment: SCA Compliance |
Strong Customer Authentication (SCA) is a European regulatory requirement to reduce fraud and make online payments more secure. SCA requires authentication to use at least two of the following three elements: 1. Something the customer knows (PIN/Password), 2. Something the customer has (Phone/Hardware token), 3. Something the customer is (Fingerprint/Face recognition). Possible values are: 0- Not required, 1- No but required, 2- Yes | ||
|
Application Classification: 1 Confidentiality |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: 2 Integrity |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: 3 Availability |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: DPIA Rating |
A data protection impact assessment (DPIA) is a privacy-related assessment whose objective is to identify and analyze certain actions or activities that might affect data privacy. Under the GDPR regulations, data protection impact assessments are mandatory in certain cases such as when profiling activities are carried out using personal data. Possible values are: 5- Very High, 4- High, 3- Medium, 2- Low, 1- Very Low, 0- Not Required |
||
|
Disaster Recovery: Recovery Point Objective (Hrs) |
Indicator to evaluate the recovery point objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
||
|
Disaster Recovery: Recovery Time Objective (Hrs) |
Indicator to evaluate the recovery time objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
||
|
Cloud Assessment: Peak Workloads |
1-No 2-Yes (Exceptionally) 3-Yes (Regularly). |
||
|
Cloud Assessment: License Eligible for Cloud |
1-No 2-Yes. |
||
|
Business Capability |
This business question requires the availability of at least 2 levels of business capabilities in your portfolio. |
||
|
Level ID |
x |
The hierarchical number of the business capability in the business capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. Necessary for the visualization. |
|
|
Name |
x |
The level ID and name of the business capability is displayed in the boxes of the heat map. |
|
|
Business Relevance |
Indicates how relevant the business capability is for the business:
|
||
|
Parent Business Capability |
x |
Every business capability on the second level of the hierarchy and lower should have a parent business capability defined. This enables the aggregation of applications that provide a lower-level business capability up to the second-level business capability. |
|
|
Reference for Application provides Business Capability |
|||
|
Business Capability |
x |
The business capability that is supported by the application. |
|
|
Application |
The application supporting the business capability. |
||
This business question provides an overview of the application roadmap and allows you to understand lifecycles of the applications including when they will be implemented or reach end-of-life.

To have meaningful data for the business question What is our application roadmap?, you must capture the following information about the applications in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
x |
The application name. |
|
|
Version |
x |
The version number for the application. It is recommended that you document major and minor release versions (<MajorVersion.MinorVersion>). |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
|
|
Strategic Application |
Indicates whether the application is strategic for the business. |
||
|
Successor Application |
All successor applications of a selected application are shown. The successor relations are visualized as black vertical arrows starting with the predecessor's end date and pointing to the successor application. |
||
|
Plan Start Date |
This is the start date of the lifecycle phase Plan. The end date will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
||
|
Pilot Start Date |
This is the start date of the lifecycle phase Pilot. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
||
|
Production Start Date |
This is the start date of the lifecycle phase Production. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
||
|
Sunset Start Date |
This is the start date of the lifecycle phase Sunset. The lifecycle phase will be set to the minimum of the next maintained lifecycle phase's start date and the lifecycle end date. |
||
|
Retired Start Date |
This is the start date of the lifecycle phase Retired. The end date will be set to the lifecycle end date. |
||
|
Lifecycle End Date |
This is the end date of the last lifecycle phase. |
||
This business question looks at the business support provided by applications to business capabilities and the organizations that use the applications. In Alfabet FastLane, the relationship between applications, business capabilities, and organizations is represented by the object class Business Support.
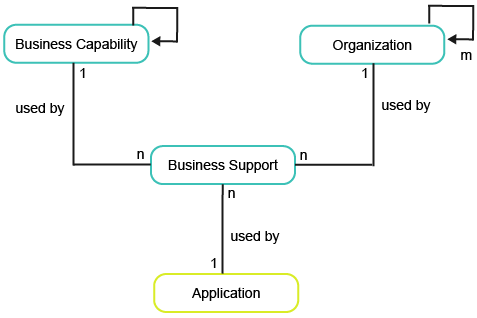
To have meaningful data for the business question What is our target architecture?, you must import and capture the following information about the applications, business capabilities, and organizations in your company:
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
x |
The application name. |
|
|
Version |
x |
The version number for the application. It is recommended that you document major and minor release versions (<MajorVersion.MinorVersion>). |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
|
|
Architecture Type |
The architecture type of the application: Possible values are:
|
||
|
Authentication |
The authentication method used for the application.
|
||
|
Development Type |
The application development type.
|
||
|
Recommendation |
The strategic recommendation regarding future investment for the application. Possible values are:
|
||
|
Strategic Application |
Indicates whether the application is strategic for the business. |
||
|
Application Assessment: Geographical Reach |
Indicator to evaluate an application's area of usage and distribution reach. This allows you to determine the geographical reach of your portfolio based on application local, regional, or global usage. .
|
||
|
Application Assessment: Mobile Capability |
Indicator to evaluate whether an application is complaint for mobile platforms. An application that fully supports all mobile platforms (Smartphones, Tablets, Smart TVs, Smart Watches, etc.) is considered to be fully mobile-compliant. An application supporting one or many but not all of the mobile platforms is considered to partially mobile-compliant.
|
||
|
Application Assessment: Multi Language Support |
Indicator to evaluate the level of support an application provides for multiple languages: 0- Unknown, 1- No, 2- Yes |
||
|
Application Assessment: Number of Users |
Indicator to evaluate sthe number of users using this application.
|
||
|
Application Assessment: SCA Compliance |
Strong Customer Authentication (SCA) is a European regulatory requirement to reduce fraud and make online payments more secure. SCA requires authentication to use at least two of the following three elements: 1. Something the customer knows (PIN/Password), 2. Something the customer has (Phone/Hardware token), 3. Something the customer is (Fingerprint/Face recognition). Possible values are: 0- Not required, 1- No but required, 2- Yes | ||
|
Application Classification: 1 Confidentiality |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: 2 Integrity |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: 3 Availability |
1-Not Critical 2-Essential 3-Critical. |
||
|
Application Classification: DPIA Rating |
A data protection impact assessment (DPIA) is a privacy-related assessment whose objective is to identify and analyze certain actions or activities that might affect data privacy. Under the GDPR regulations, data protection impact assessments are mandatory in certain cases such as when profiling activities are carried out using personal data. Possible values are: 5- Very High, 4- High, 3- Medium, 2- Low, 1- Very Low, 0- Not Required |
||
|
Disaster Recovery: Recovery Point Objective (Hrs) |
Indicator to evaluate the recovery point objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
||
|
Disaster Recovery: Recovery Time Objective (Hrs) |
Indicator to evaluate the recovery time objective in hours: 0-< 1 Hr 1-1-2 Hr 2-2-3 Hrs 3-3-5 Hrs 4-5-12 Hrs 5-> 12 Hrs. |
||
|
Cloud Assessment: Peak Workloads |
1-No 2-Yes (Exceptionally) 3-Yes (Regularly). |
||
|
Cloud Assessment: License Eligible for Cloud |
1-No 2-Yes. |
||
|
Business Capability |
This business question requires the availability of at least 2 levels of business capabilities in your portfolio. |
||
|
Level ID |
x |
The hierarchical number of the business capability in the business capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. Necessary for the visualization. |
|
|
Name |
x |
The level ID and name of the business capability is displayed in the boxes of the heat map. |
|
|
Business Relevance |
Indicates how relevant the business capability is for the business:
|
||
|
Parent Business Capability |
x |
Every business capability on the second level of the hierarchy and lower should have a parent business capability defined. |
|
|
Reference for Application provides Business Capability |
|||
|
Business Capability |
x |
The business capability that is supported by the application. |
|
|
Application |
The application supporting the business capability. |
||
|
Organization |
|||
| Name | |||
|
Parent Organization |
Every organization on the second level of the hierarchy and lower should have a parent organization defined. |
||
|
Reference for Application uses Organization |
|||
|
Organization |
x |
The organization that uses the application. |
|
|
Application |
The application used by the organization. |
||
The business question How will IT failure impact our business? provides a high-level end-to-end view of your IT technology landscape. This offers insight to which business capabilities will fail if servers and applications go offline.
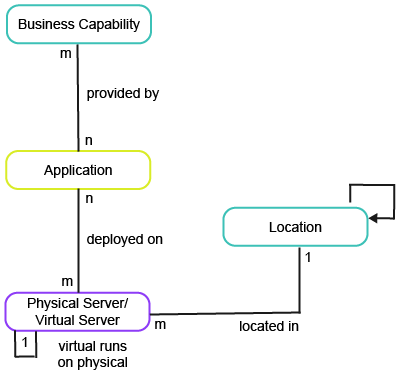
To have meaningful data for the business question How will IT failure impact our business?, you must capture the following information about the business capabilities, applications, physical servers, virtual servers, and locations relevant for this business question in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Business Capability |
|||
|
Level ID |
The hierarchical number of the business capability in the business capability hierarchy. For example: 1, 1.1, 1.1.1, 1.2, 1.2.1, etc. |
||
|
Name |
x |
The business capability's name. |
|
|
Parent Business Capability |
The parent business capability in the business capability hierarchy. |
||
|
Business Relevance |
Indicates how relevant the business capability is for the business:
|
||
|
Application |
|||
|
Name |
x |
The application name. |
|
|
Version |
x |
The version number for the application. It is recommended that you document major and minor release versions (<MajorVersion.MinorVersion>). |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
|
|
Architecture Type |
The architecture type of the application: Possible values are:
|
||
|
Authentication |
The authentication method used for the application.
|
||
|
Development Type |
The application development type.
|
||
|
Recommendation |
The strategic recommendation regarding future investment for the application. Possible values are:
|
||
|
Virtual Server |
|||
|
Name |
The virtual server's name. |
||
|
Version |
x |
The version number for the virtual server. |
|
|
Start Date |
x |
The start date is the date when the virtual server is actively used. |
|
|
End Date |
x |
The end date is the date when the virtual server is no longer used. |
|
|
Object State |
x |
Describes the use of the virtual server in the real word. This can be understood as the operational status of the virtual server. Possible values are:
|
|
|
Status |
x |
Specifies the approval status of a virtual server and determines whether or not the vitual server can be edited or deleted. Possible values are:
|
|
|
Server Type |
Specifieds whether the server is an application server, Web server, mail server, FTP server, collaboration server, or another type of server. |
||
|
Physical Server |
The physical server that the virtual server runs on. |
||
|
Physical Server |
|||
|
Name |
x |
The physical server's name |
|
|
Version |
x |
The version number for the physical server. |
|
|
Start Date |
x |
The start date is the date when the physical server is actively used. |
|
|
End Date |
x |
The end date is the date when the physical server is no longer used. |
|
|
Object State |
x |
Describes the use of the physical server in the real word. This can be understood as the operational status of the physical server. Possible values are:
|
|
|
Status |
x |
Specifies the approval status of a physical server and determines whether or not the physical server can be edited or deleted. Possible values are:
|
|
|
Location |
The location where the physical server is deployed. |
||
|
Location |
|||
|
Name |
x |
The location's name. |
|
|
Parent Location |
The parent location indicates where a location can be found and serves as the full location name. |
||
This business question examines the application portfolio and the business data that is created, read, updated, or deleted by the applications.
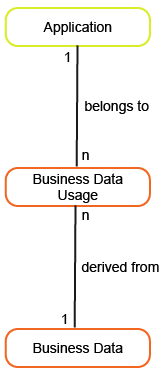
To have meaningful data for the business question Where do we use sensitive data?, you must capture the following information about the applications and business data in your company.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
|||
|
Name |
x |
The application name. |
|
|
Version |
x |
The version number for the application. It is recommended that you document major and minor release versions (<MajorVersion.MinorVersion>). |
|
|
Start Date |
x |
The start date is the date when the application is actively used. |
|
|
End Date |
x |
The end date is the date when the application is no longer used. |
|
|
Object State |
x |
Describes the use of the application in the real word. This can be understood as the operational status of the application. Possible values are:
The object state should be changed from Plan to Active once the application's start date is reached. It should be changed to Retire when the application's end data is reached. |
|
|
Status |
x |
Specifies the approval status of an application and determines whether or not the application can be edited or deleted. Possible values are:
|
|
|
Business Data |
|||
|
Name |
x | ||
|
Version |
x | ||
|
Data Category |
x | The data category that the business data is assigned to. | |
|
Data Classification |
Classification of the business data based on data protection requirements. Possible options are: Confidential - Non-Personal Data, Confidential - Personal Data, Restricted, Unrestricted, and Unknown |
||
|
Data Classification:DPIA Rating |
A data protection impact assessment (DPIA) is a privacy-related assessment whose objective is to identify and analyze certain actions or activities that might affect data privacy. Under the GDPR regulations, data protection impact assessments are mandatory in certain cases, such as when profiling activities are carried out using personal data. 5-Very High 4-High 3-Medium 2-Low 1-Very Low 0-Not Required. |
||
|
Business Data Usage |
|||
|
Business Data |
x |
The business data that is used. |
|
|
Application |
x |
The application that uses the business data. |
|
|
Create |
CRUD value that describes that an application creates a referenced business data. |
||
|
Read |
CRUD value that describes that an application reads a referenced business data. |
||
|
Update |
CRUD value that describes that an application updates a referenced business data. |
||
|
Delete |
CRUD value that describes that an application deletes a referenced business data. |
||
|
Data Category |
|||
|
Name |
x | ||
|
Parent Data Category |
The parent data category that the data category is assigned to in the data category hierarchy. |
||
|
Description |
Information about the category of business data that will be assigned to the data category. |
||
This business question provides a top-down portfolio analysis for cloud migration in order to understand the applications that are best suited for migration based on cloud relevance and cloud readiness indicators.
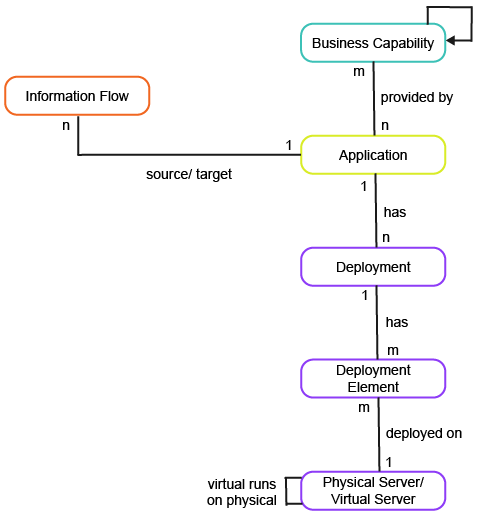
To have meaningful data for the business question What are our cloud focus areas?, you must capture the following information about the applications, information flows, business capabilities, and servers in your company.
| Class | Attribute | Mandatory | Explanation |
|
Application |
Name |
Necessary for the visualization. |
|
|
Version |
Necessary for the visualization. |
||
|
End Date |
x |
The end date of the application is used to calculate the Application End of Life indicators for the cloud readiness score and the cloud relevance score. |
|
|
Cloud Migration Strategy |
x |
The strategy to migrate the application to the cloud. Values include: Retain, Rehost, Rearchitect, Rebuild, Migrated, Unknown |
|
|
Architecture Type |
x |
The architecture type is used to calculate the cloud readiness score. Values include: Unknown, Mainframe, Distributed, Client Server, Stand Alone, Cloud-Based, External Webpage |
|
|
Authentication |
x |
The authentication type is used to calculate the cloud readiness score. Values include: Unknown, Multi-Factor & SSO, Multi-Factor, Client Server, SSO, Bsic Access, Autonomous, No Authorization |
|
|
Subject to Compliance Regulation |
x |
Indicates whether the application is subject to compliance regulations. Used to calculate the cloud relevance score. |
|
|
Peaks in the workload |
x |
Indicator used to contribute to the cloud relevance score. |
|
|
License Portability |
x |
Indicator used to contribute to the cloud relevance score. |
|
|
Current Year OpEx |
x |
The application's current year total operational expenditure (OpEx) is defined as the sum of the application costs for the current year. |
|
|
Business Capability |
Business Relevance |
x |
Indicates how relevant the business capability is for the business. Contributes cloud relevance score. |
|
Application |
x |
Application providing the business capability |
|
|
Information Flow |
Object State |
Describes the operational status of the information flow. Information flows with a retired object state are ignored. |
|
|
Source Application, Target Application |
x |
An information flow requires an application that is the source and target of the connection. The number of information flows for which the application is the source or target contributes to the cloud readiness score. |
|
|
Virtual Server |
Physical Server |
The virtual server runs on a physical server. Whether the application is running on a virtual server impacts the cloud readiness score. |
|
|
Object State |
Describes the operational status of the virtual server. Virtual servers with a retired object state are ignored. |
||
|
Physical Server |
Object State |
Describes the operational status of the physical server. Physical servers with a retired object state are ignored. Whether the application is running on a physical server impacts the cloud readiness score. |
|
This business question supports the planning of a migration strategy for each application in your cloud portfolio based on an understanding of the impact of migration to business capabilities and the IT ecosystem.

To have meaningful data for the business question What is our cloud migration strategy?, you must capture the following information about the applications in your company. It is recommended that application data is complete and that the application's information flows and the business data they transfer as well as the components that the applications use are captured.
| Class | Attribute | Mandatory | Explanation |
|---|---|---|---|
|
Application |
Name |
||
|
Version |
|||
|
Cloud Migration Strategy |
x |
The strategy to migrate the application to the cloud. Possible values include:
|
|